In the society we live in, our digital information is everything, and it’s all on our phones. It can tell someone who we are, what we have, where we are, and where we’re going. So, if I told you to give a stranger your phone right this moment so that the government could look at all of your information, would you do it? In a time where government mistrust is arguably at an all-time high, I doubt many people would. But what if that stranger didn’t even give your phone to the government? What if they kept all of your information for themselves? This seems improbable to ever happen right, you would never give up our phone like this? Well, the reality is, this could happen, and you may not have a choice in the matter.
This is a time where nearly all of our information is tied to our phones, and most people protect that information as best they can. There’s a reason people freak out when they lose their phone. Nobody I know would willingly give it up, but the FBI might give us no choice. They want Apple to create a ‘backdoor’ into the iPhones that so many people use today, for a reason they claim to be true, but it is one that is questionable when put under examination. What the FBI wants would effectively release most of the world’s population’s data into the wild. Data that would be ripe for the picking for anyone who has the knowledge to access it, and the ramifications would be catastrophic.
In late 2015, Syed Rizwan Farook and his wife Tashfeen Malik killed 14 people and injured 22 more in a shooting that took place in San Bernardino, California. The day after the shooting occurred, the FBI searched the home of the couple and recovered an iPhone 5c running iOS 9, this phone was secured with a 4 digit pin number. This pin number is perhaps one of the most basic forms of encryption, or “a mathematical algorithm to scramble electronic messages”. This pin was the only thing preventing the FBI from gaining access to this iPhone, which they believed to have had data that would give them information about other terrorists Syed or his wife might have been connected to. However, the iPhone in question had built in security which would erase all data on the phone after 10 incorrect attempts at guessing the passcode were made.
The FBI asked Apple to assist them with their efforts to unlock the phone, to which Apple happily complied. Apple themselves reported that for some time, they helped the FBI troubleshoot ways in which to get data off of the phone, but unfortunately the FBI made a mistake that caused Apple’s suggestions to be irrelevant. It was at this point that the FBI asked Apple to create a new version of the iOS 9 operating system in which the FBI could bypass security and therefore gain access to all of the data contained on the phone.
Apple reportedly discussed this possibility for an extended period of time before they came to the conclusion that this was a terrible idea. They weren’t concerned with the possibility of whether or not what the FBI was suggesting was possible, but were deeply worried about the possible ramifications such a software would have on the world. As Apple CEO Tim Cook explains,
“In the wrong hands, this software – which does not exist today – would have the potential to unlock any iPhone in someone’s physical possession”.
To Apple and many others, including myself, this is simply too high of a price to pay for data that may or may not contain information that could link Syed Farook and his wife to other terrorist organizations.
The FBI however, sees this differently. They don’t care whether there is a chance, no matter how high, that the information on the phone is useless. If there is even a sliver of a chance, they are willing to accept the consequences of obtaining the information, and this is a huge problem. The FBI basically outright refuses to listen to the logical reasoning of those who disagree, and some think that this might be a conscious effort on the FBI’s part to cover up ulterior motives. This, among other factors, has led numerous others to question whether the FBI and other government agencies can be trusted in this matter.
One of the major arguments made against the FBI is that they aren’t going to do what they are promising they will. The FBI claims that they wish to use this new operating system, which again, hasn’t yet been created, on only the one iPhone in the San Bernardino case. FBI Director James Comey says, “We simply want the chance, with a search warrant, to try to guess the terrorist’s passcode without the phone essentially self-destructing and without it taking a decade to guess correctly”. That sounds good on paper, but at the same time it is very hard to believe. I find it difficult to accept that the FBI would effectively ‘throw away’ this invaluable technology after only one use. The access this software would give the FBI and more generally, all law enforcement across the United States would no doubt help them immensely in solving crimes and perhaps preventing them. However, far too much access will be gained, more than anyone should have, including government agencies.
Everyone, especially after the past few years, has most likely heard about the NSA. After the Edward Snowden incident, in which he leaked secret government information about how they were listening in on our phone calls and recording our data, do you really want the NSA to have access to a backdoor leading to ALL of your information? The NSA is like the FBI, there is no chance that they would pass up on software that gives them access of this degree. Just ask Michael Hayden, Former Director of the NSA, “When you put a backdoor into everything, as the former Director of the NSA, I’m going ‘thank you Lord. Because even though that backdoor is not intended for me, and even though it might be really well constructed, and even though it may take me a long time, good intelligence services have now been given one additional potential entryway into your data and mine”.
These intelligence services aren’t restricted to domestic agencies either. I’ll let Aziz Gilani, current partner at Mercury Fund with 15 years of software and internet experience explain, “Once Apple implements a backdoor to the iPhone, foreign governments will also demand access to encrypted information on their seized iPhones. Even if you completely trust the U.S. government, how do you feel about the Chinese, Russian, Iranian, or Syrian governments having the power to access encrypted data from their citizens?”. Obviously this is a less than optimal situation, giving these governments the power to access their respective population’s information is likely more harmful than if our government had this power. As it is, the U.S government having this power is a situation that should be avoided. So ask yourself this, does this really seem like security is being heightened when encryption is weakened?
You could argue that this is all speculation, but there’s no denying the fact that there are hundreds of phones across the nation that law enforcement agencies want Apple to unlock. How can the FBI say that this new operating system will only be used on one phone when that is clearly not true? If Apple unlocks this iPhone for the FBI, then there is no doubt that a precedent will be set. After Apple unlocks Farook’s phone, what stops other law enforcement agencies from getting Apple to do the same? John Oliver from Last Week Tonight refers to this precedent as “opening Pandora’s Box”, even if the new software was kept in the hands of Apple and nobody else got a hold of it, how can they say no to any other agency after complying with the FBI?
Even in light of all of this, there are still those who say that this new software could be written to work on only one iPhone, more specifically Syed Farook’s iPhone. However, this is simply untrue. Tim Cook who has far more expertise, knowledge, and experience in this field than most others, warns consumers, “Once created, the technique could be used over and over again, on any number of devices”. Security technologist Bruce Schneier agrees, writing “the hacked software the court and the FBI wants Apple to provide would be general. It would work on any phone of the same model. It has to”. The general consensus among technology experts seems to be that if this software were created, there is a very slim chance it would be utilized only once.
Even if the FBI only used this technology once, there is no guarantee that the software would remain solely in the hands of Apple. In a letter to Apple customers on this controversy, Apple explains,
“Of course, Apple would do our best to protect that key, but in a world where all of our data is under constant threat, it would be relentlessly attacked by hackers and cybercriminals. As recent attacks on the IRS systems and countless other data breaches have shown, no one is immune to cyberattacks”.

This relentless attacking by hackers would no doubt end with someone obtaining the master key to all iPhones, which shouldn’t be in the hands of the government much less a random hacker. It would only be a matter of time before our information and important data would be at the fingertips of criminals looking to exploit it, and this isn’t even the half of it. According to Ira Kalb, Assistant Professor of Clinical Marketing at the University of Southern California, “government officials and company executives around the world use the iPhone simply because it has better encryption than other choices. Once the encryption is decoded, could that compromise our security more and expose companies to more industrial espionage?”. Points like these are those that the FBI seems to be outright refusing to acknowledge, by opening a backdoor to all iPhones we could be doing more damage to our security than good, all while reducing privacy to a minimum.
Another major point that a lot of people seem to not understand is just how much information is connected to our phones. This controversy is so important because of what we stand to lose. Our phones don’t just contain our pictures, texts, etc. Off the top of my head I can think of a few operations we use our phones for that could seriously put us at risk in different ways if the wrong person had access. For example, our phones are connected to our bank accounts, emails that could contain secrets about government or corporate business that might prove catastrophic to those entities, or even home security systems that could be exploited. Nowadays your location is even tracked by your phone. However, the implications of a backdoor don’t stop at individuals’ information. Utilizing the new operating system, hackers could even gain access to the power grid,
“Think about something that happens to the infrastructure, where there’s a power-grid issue. Think about the people who are on a medical device that depends on electricity … these aren’t fantasy things by any means”. – Tim Cook
It isn’t only our digital wellbeing that is at risk, there is so much more on the line than most people realize, including the FBI.
Weakening encryption on phones and devices in general makes us highly more susceptible to all of these things and more, yet some continue to relentlessly push for ‘increased security’. What these people fail to understand is that there isn’t an indirect correlation between encryption and security. If one increases, the other doesn’t necessarily decrease. In reality, if encryption is weakened, security will likely decrease as a result. However, agencies such as the FBI only seem to think of security in the immediate sense instead of in the long term. Thwarting a terrorist today by utilizing the backdoor might stop one threat, but countless other threats will be created in the process. It is a terrible trade to make. The FBI simply does not know what it is talking about, Tim Cook does, “Then you’re back where you started “if the new operating system is released), except worse off, because everybody else’s crypto is now more vulnerable, with their data ripe for the pillaging. You’re only punishing the good guys”.
In addition to all of these implications, our economy could possibly take a hit. It is highly imperative that American companies remain competitive in foreign markets, both for “economic growth and nation security”.
“The U.S. economy will not grow if it is unable to protect its assets” – CNN
Competitiveness isn’t the only factor here though, if a backdoor is created then American companies will become susceptible to hackers too, and they could lose vital data that aids American economic growth.
Presented with all of this information, there are even those in the government who are strongly against drastically decreasing encryption in favor of ‘heightened security’, especially in this way. In fact, the majority of the government has voted for increased encryption and decreased surveillance multiple times in the recent past.
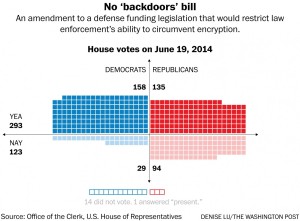
For those who aren’t familiar with the term, circumvent means ‘to find a way around’. Meaning that this bill was proposed in order to “restrict law enforcement’s ability to find a way around encryption”. The fact that this bill was even proposed is highly significant, showing that law enforcement isn’t 100 percent backed, blindly, by the government. What is even more significant is that this bill passed with an overwhelming majority vote in the House, and later went on to be signed into law by President Obama. There was barely any divide between the Democrats and Republicans either, which we all know rarely happens. As can be seen, both parties were largely in favor of this bill, which holds great value, especially because this bill was approved only 2 years ago.
With the current controversy this bill shows that the majority of the government is in favor of protecting our privacy and information, which largely takes away from the FBI’s credibility in this matter, as they aren’t supported by the majority of the government they work for. One of the FBI’s major talking points is how our national security is at risk with heightened encryption, but one of Congress’s largest responsibilities is to protect the population through legislation, and this bill shows that they strongly disagree with the FBI. But this isn’t the only piece of legislation that demonstrates this point.
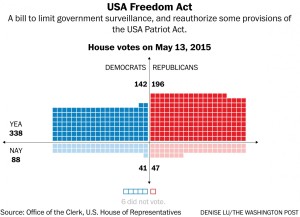
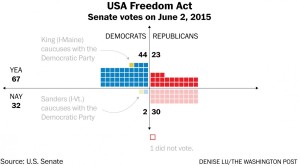
The USA Freedom Act is even more recent than the ‘No Backdoors Bill’, being only a year old. Slightly differing from the aforementioned bill, this Act sought to limit government surveillance, which is one of the greatest threats posed by radically decreasing encryption through the use of a backdoor. Our right to privacy is not one that should be taken lightly, and the software that the FBI wants Apple to create could be perhaps one of the greatest breaches of privacy ever imagined. No doubt it was influenced by the Edward Snowden incident, which greatly reduced the public’s trust in the government. Much like the ‘No Backdoors Bill’, this Act won in the house with overwhelming numbers, 338 yea to 88 nay. After winning in the house, this legislation went onto win a majority vote in the senate as well, with a tally of 67 yea to 32 nay. Also like the previously mentioned bill, the fact that this Act is very recent helps to show where the government stands currently on this matter. Some congressmen and politicians have even taken time to speak out against decreasing encryption individually.
Last year, U.S. Representatives Will Hurd and Ted Lieu wrote a letter to the Director of the FBI, expressing their lack of approval for the actions the FBI wanted to take. They wrote, “We strongly, but respectfully, disagree with the FBI’s proposal to force privacy sector companies to weaken the security of their products and services. As computer science majors… we strongly urge the FBI to find alternative ways of addressing the challenges posed by new technologies”. In case you were wondering why they should be believed as opposed to the FBI, it is because as they mention, they have computer science degrees. They understand that this carries weight, and they also understand that the FBI have near to no credibility in this entire controversy. These Representatives no doubt worded what they said carefully, knowing that they would automatically have the upper hand when it comes to who the reader believes, and they want the FBI to know it.
These two Congressmen go on to reinforce one of the major points made in this entire controversy. This being that if the FBI uses this software, then hackers can too,
“the same backdoor that lets in FBI agents can be used by hackers too”.
These two Congressmen aren’t the only government officials speaking out individually however. Senator Lindsey Graham, at the beginning of this controversy, was entirely set on the idea of decreasing encryption and gaining access to the iPhone found at the home of Syed Farook. But after a simple briefing by technology experts on the facts surrounding the matter, the senator pulled a complete 180. He later went on to speak out against creating a backdoor and argued that it would have a negative impact on our world. Even former NSA Director Michael Hayden, whom I mentioned earlier, doesn’t find truth in what the FBI is trying to say. He explains that, “My point is, American security, on balance, is better served with unbreakable encryption”. This is coming from a man who used to run the agency that would almost definitely use a backdoor the most. The FBI and NSA both seem to believe that American security is tighter with little to no encryption, but if the Former Director of the NSA goes directly against those beliefs, how can you help but question them?
At numerous points throughout this article, I have called into question whether or not we can trust the FBI and their motives. Most of the things they say turn out to be either outright untrue, or empty statements without any factual backing. One of the best examples of this is seen in a letter that FBI Director James Comey wrote to the public regarding this controversy. Throughout the letter it is apparent that the FBI have no facts to back up their claims. In fact, most of the letter is comprised of plays at tugging on the readers emotions. This is all an obvious attempt to gain the sympathy of the reader and gather support for the FBI’s views.
For example, Comey states, “So I hope folks will remember what terrorists did to innocent Americans at a San Bernardino office gathering and why the FBI simply must do all we can under the law to investigate that”. He words it as though you are a terrible person if you don’t ‘remember’ what terrorists did in this incident. He further tries to guilt trip the reader by saying,
“Maybe the phone holds the clue to finding more terrorists. Maybe it doesn’t. But we can’t look the survivors in the eye, or ourselves in the mirror, if we don’t follow this lead”.
All this statement does is put on display the shortsightedness of the FBI. Comey first acknowledges that there is a possibility that the phone contains nothing, but then continues to explain that no matter what they have to crack the phone regardless. He shows how the FBI are fixed on only this case, and not the overall wellbeing of the American people, or for that matter, the world.
This could all indicate that the FBI is simply attempting to use this case as a base to jump off of in order to get legislation passed. Legislation that would give law enforcement free range and access to our phones, similar to the access they now enjoy to our homes (provided they have a search warrant). Further evidence to support this is shown through the past attempts that have been made to do so.

For decades law enforcement has been trying to access our phones, as can be seen by their attempt at putting a device called the “Clipper Chip” into service. This chip was designed to be placed in telephone handsets, and “would encrypt digital communications while allowing the government to keep a key”. The Clipper Chip posed many of the same ramifications that we could be facing in the near future, such as American technology products not looking appealing to foreign consumers, and it was shot down for reasons such as this.
So if we didn’t think it was a good idea then, why should we think it is now when it is on a much larger and more terrifying scale? The fact is we shouldn’t, but the FBI is trying to convince us of the opposite. Law enforcement has been looking for ways to get into our phones for years, and they might have seen their opportunity in the San Bernardino case and taken it.
No matter what the FBI’s true motives are, many still believe that finding information about terrorists worldwide by utilizing a backdoor far outweighs the negatives. However, what they don’t realize is that the FBI may not be able to retrieve the information they need. Even with access to the phones of terrorists, terrorist organizations, or everyday criminals, there are other ways to encrypt data. Representatives Will Hurd and Ted Lieu write, “terrorists trying to avoid the FBI can easily download software tools that make their communications private anyway”. Tim Cook builds upon this, adding that
“there’s no legislating away encryption. The bad guys will remain encrypted as ever, no matter what. “The Internet doesn’t have boundaries. You can wind up getting an app from Eastern Europe or Russia or wherever, it doesn’t matter which country, just outside the United States. And that app would give you end-to-end encryption”.
Essentially, both of these statements implicate that even if the FBI can compel Apple to create the software they desire, it will be useless to the FBI. While it is true that the FBI would be able to access Farook’s phone, terrorists worldwide would learn quickly and encrypt themselves through other methods. This means that in the end, no real progress will have been made and everyone else will be worse off in the meantime.
In the society we live in, our phones are a part of us, and we need to protect them and the information they carry as much as we need to protect ourselves. The two go hand in hand. We have a right to privacy, and even more so than that we have the right to protect ourselves. If the FBI is able to force Apple to create an operating system that renders our encryption utterly useless, we lose both of those rights, and stand to lose much more. Decreasing encryption is not going to increase security. It may help to protect against one physical threat, but the damage it will cause to our infrastructure will be enormous. The FBI needs to realize this and put aside their aspirations of increased surveillance for the good of not only the American people, but also the world.